Automation, automation, automation. It’s a buzzword in the IT and security industry at the moment. Gartner highlights that security process automation is one of the key trends to emerge from 2020, in large part due to a shortage in skilled security practitioners. And this is not the only driver: “with the size of data multiplying every day, it is eminent that automation is integrated to give more sophisticated control over the information.”
There’s good reason for this move towards automation: when security tasks are automated we gain speed, scalability and reliability. While automation has become commonplace in many areas of IT and network security, there are levels of the Network Security Protection Pyramid where it has been ignored. To our detriment. Read on and I’ll explain how security automation at the infrastructure layer of the network has the biggest impact on overall risk reduction to network security. Plus, it lowers total cost of ownership (TCO) compared to what you’re doing today!
What is the Network Security Protection Pyramid?
We need to think of network security protection in terms of a pyramid or hierarchy. At the bottom of the pyramid we have the foundational layers of network security: Deploy and Configure. Here are technologies and practices offering the greatest risk reduction—like infrastructure configuration, posture management, patching and configuring. At the top of the pyramid are the Assess and Respond layers with products like advanced threat detection tools, which are important but remove less risk if the underlying layers aren’t solid.
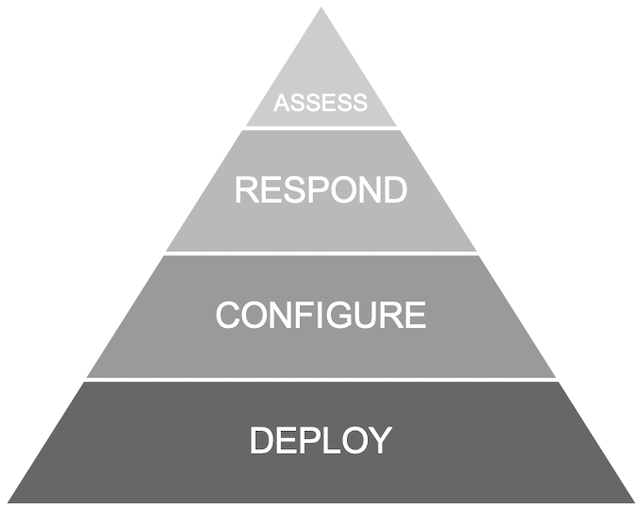
The importance of a strong foundation
Nowadays it’s easy to get excited about the innovative cybersecurity tools at the top of the network security protection pyramid. They use cool technology; they’re the bright, shiny objects. Technologies like SIEM (security information and event management) and SOAR (security orchestration, automation and response). Or, how ML (machine learning) and AI (artificial intelligence) bring advantages in the areas of data analysis and remediation. There’s no denying these technologies represent great advances, especially in terms of automation. In reality though, the infrastructure layer of the pyramid is the foundation on which the rest of the security stack relies. In other words, unless you get the security basics right, it doesn’t matter how cool your other security tools look or act.
Why automation is key to the protection pyramid
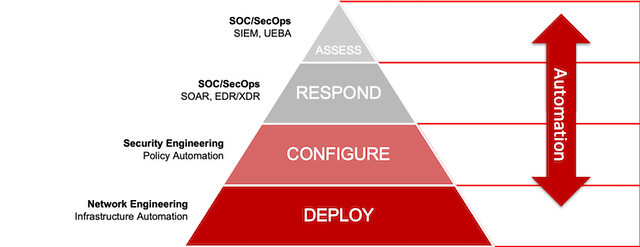
While we’re comfortable introducing automation at the top layers of the protection pyramid—with technologies like SIEM and SOAR—it shouldn’t stop there. That’s because when we think of the Deploy level, all we see is fixed equipment and boxes. But, if we begin to think of this infrastructure as software-defined or virtualized, then we can introduce automation. Network security automation has the potential to simplify workflows and improve uniformity and accuracy in network security. So, if it is implemented at the most foundational level of Deploy and Configure, we’ll begin to see much greater risk reduction overall.
How to automate network firewalls
So, let’s get practical and take network firewalls. These are classic examples of infrastructure that sit firmly at the base of the pyramid. But even if we virtualize them, we still have an issue. While we have automation tools for the Respond and Assess layers, when it comes to Deploy and Configure, network engineers are left to figure out infrastructure automation on their own. There are no truly integrated solutions or tools; nothing comes out of the box for virtual firewalls. This leads to a DIY nightmare and one of the main reasons that automation is slow to take on in this area.
To implement automation in network firewalls we need to start by automating the migration of physical firewalls to virtual ones. Operations that would normally be performed manually—generating an ISO image, defining VM settings, bootstrapping, provisioning, for example—need to be implemented seamlessly without requiring custom scripts. And once the virtual firewalls are deployed, we need to automate additional configuration, ongoing management and software upgrades, too.
The benefits of automating the full protection pyramid
It’s no wonder that automation is one of the current superstars in security. It brings a level of efficacy, speed and agility that we haven’t seen historically. But, that shouldn’t be limited to the Assess and Respond layers. When we take that same automation to the base of the pyramid the advantages really begin to add up:
- Simpler, centralized, more user-friendly management of operations,
- Faster delivery of new services and capabilities,
- Dynamic, rapid changes to network firewall capacity thanks to virtualization,
- And reduced costs as we move away from capital expenditure for hardware to a pay-per-use, software-based model.
If we’re going to make the most of automation and dramatically reduce the risk of a network breach, we need to start with the infrastructure. As we’ve seen, making improvements to the most foundational element of network security brings the greatest reduction of risk. In other words, start with virtualizing your network firewalls so your threat protection increases to any scale, while also lowering your overall TCO. Then, shift your focus to automation at the foundational layer of the network security protection pyramid, and enjoy these many other benefits too.
