What do you mean by network security automation?
Network security automation can mean many different things but for us it is the practice of automatically migrating physical, or hardware, network security appliances to virtual ones and then being able to manage and scale this software-defined security for future needs. When we say network security automation, we’re talking about operations which would normally be performed manually when you migrate to virtualized security —like generating an ISO image, defining VM settings, bootstrapping, provisioning—instead being implemented seamlessly without requiring DIY or custom scripts.
Why opt for network security automation?
As things stand today, every large network has tens, or even hundreds, of network security appliances, like firewalls, scattered about, each one protecting different tenants and their environments. All of these network firewalls are physical appliances, which means they are a fixed resource that is complex and expensive to deploy, manage and operate. In general, current network security architectures do not scale and lock you in.
Network security automation is a powerful solution for simplifying workflows and improving uniformity and accuracy when you virtualize network security services. Automation increases the speed of operations, reduces human error and quickly makes updates to whole sets of virtual machines.
With network security automation, you get simple and scalable virtualization plus these benefits:
- save time thanks to efficacy and zero touch network operations
- save money because you don’t have to invest in hardware upgrades
- scalability and agility of a software-based system
- gain more sophisticated control over information
- deliver the biggest impact on overall risk reduction because you’re improving the infrastructure (foundational) layer of the network.
What’s so difficult about network security automation?
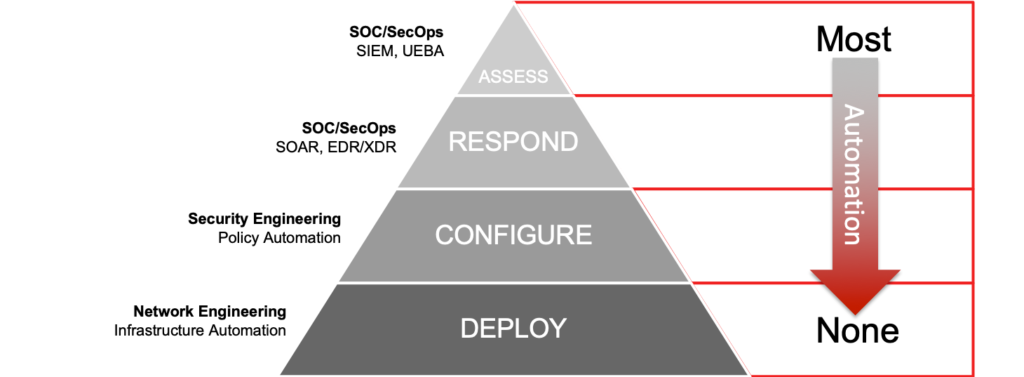
While we have automation of the Respond and Assess layers of the network security protection hierarchy, when it comes to Deploy and Configure (where the infrastructure sits), network engineers are left to figure out automation on their own. There are no truly integrated solutions or tools; nothing comes out of the box to automate the infrastructure layer. This leads to a DIY nightmare and one of the main reasons that automation is slow to take on in this area.
Let’s use network firewalls as an example. To adopt network security automation at the infrastructure layer, you need to virtualize the network firewalls and it needs to be simple to migrate, easy to manage and adjustable as needed. You must be able to leverage the same type of virtual firewall instances used in the cloud and have an automatic way of creating and deploying exact replicas of the physical firewalls. It must be so straightforward that it clearly saves you time and effort and brings you operational and economic efficiencies. In other words, you need a platform which automates the migration of physical firewalls to virtual ones.
What are the benefits of network security automation?
Automation at the infrastructure level of your network security stack means virtualization becomes simple and attainable for everyone.
With network security automation you benefit from:
- Rapid time to deployment: This is one of the biggest advantages of automation at the infrastructure level. No need for scarce engineering skills, no need to reconfigure the network architecture. A turnkey automated virtualization platform is ready to deploy out of the box and takes a matter of minutes to set up. This enables dynamic, rapid changes to network security capacity and faster delivery of new services and capabilities to customers.
- Significantly reduced TCO: Automating your migration to virtualization removes the CAPEX investment associated with physical appliances, and automated virtualization minimizes the need to use costly DevOps resources. Plus, you only pay for the capacity you need, driving down overall cost even more.
- Reduced need for training: There’s no ongoing training needed as you get to keep your current or preferred security providers, and the system is integrated with your security and operations tools.
- Cloud-like experience: Like so many other areas of IT and cybersecurity, this new paradigm means that network security can be managed like the cloud, making it familiar and accessible to all team members. Spinning up a new firewall, for example, becomes “as easy as the cloud.”
- Simple, centralized, more user-friendly management: You cut the average provisioning time and complexity per event since all network security are controlled from a single, central UI.
How do I plan for successful network security automation?
Consider these steps as you plan your network security automation.
1. What’s your goal?
Having a clearly defined operational goal will make your project more successful. What are your functional requirements? What is achievable and realistic? Make sure the means aren’t too complicated or expensive to be practical.
2. Do you have to automate everything?
Make sure your scope is also clearly defined and achievable. Projects that templatize common access (VPN connectivity, third-party access, new server setup, etc.) are likely to succeed. However, do you really need to include one-off and infrequent processes? Use the 80/20 rule here: focus on the 80% who will benefit from a readily achievable project, rather than using precious resources on including the other 20%.
3. Take another look at technical standards
In any automation project, you will probably have to sacrifice some things for gains in efficiency. If you revisit your technical standards through the lens of your automation goals, you can actually reap efficiency gains with little practical impact on overall control.
Should I opt for network security automation now?
Think of network security in terms of the protection hierarchy and consider where you can automate with most impact. At the bottom of the pyramid we have the foundational layers of network security: Deploy and Configure. Here are technologies and practices offering the greatest risk reduction—like infrastructure configuration, posture management, patching and configuring. Automation of the Deploy and Configure layer can make a huge difference to your network security. At the top of the pyramid are the Assess and Respond layers with products like advanced threat detection tools. Automation will bring gains to the SOC team’s ability to shut down attacks in a timely manner.
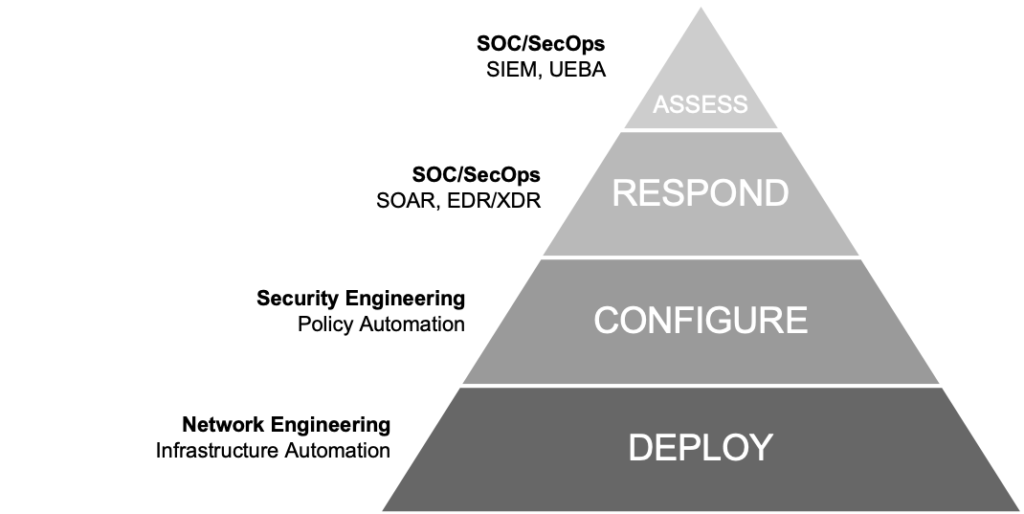
It’s easy to get blinded by the latest and greatest cybersecurity tools in the Assess and Respond layers of the pyramid; everyone’s talking about them, they use sexy technology, they’re the new, shiny objects. However, we all know that when it comes to cyber warfare, adopting the trendiest tool is no match for sound IT hygiene. The infrastructure layer of the pyramid is the foundation on which the rest of the security stack relies. Unless you get the security foundation right, it doesn’t matter how cool your other security tools look or act.
Network security automation needs to be applied to the base of the pyramid in Deployment and Configuration first if we’re to see the performance, scalability and cost savings we’re looking for. So, yes, you need to start with network security automation now so you can benefit from virtual security services without extra overhead!
Featured Resource

